- the packer only support x64 exe's (altho planning to make x32 version but idk when it'll be done)
- no crt imports
- api hashing library ( custom getmodulehandle and getprocaddress )
- direct syscalls ( for the part that i do the ntdll unhooking )
- ntdll unhooking from \KnownDlls\
- support tls callbacks
- support reallocation in case of needed ( the image is mapped to the preferable address first )
- no rwx section allocation
- support exception handling
- uses elzma compression algorithm to do the compression (reducing the final file size)
- its local run pe, so it support arguments
- fake imported functions to add more friendly look to the iat
- you can download from here or compile the code manually
- supports only 1 input:
x64 native exe files. - supports 3 outputs:
- dll :
Example "rundll32.exe DllPP64.dll Atom" (Using "Atom" is a must to run your payload - this is the name if the exported function in the dll)can be hijacked / injected into other process
- exe :
this output is the default (with console - for binaries like mimikatz)
- no console exe
for binaries like a c2 agent
- dll :
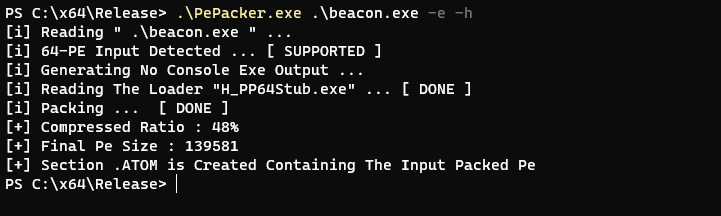
[#] Usage : PePacker.exe <Input x64 exe> <*Output*> <*Optional Features*>
[#] Output :
-d : Output The Packed Pe As A x64 Dll File
-e : Output The Packed Pe As A x64 Exe File (Default)
[#] Features :
-h : Hide The Console - /SUBSYSTEM:WINDOWS
Example:
PePacker.exe mimikatz.exe : generate exe packed file
PePacker.exe mimikatz.exe -e : generate exe packed file
PePacker.exe mimikatz.exe -e -h : generate hidden exe packed file
PePacker.exe mimikatz.exe -d : generate dll output
- x32 support
- reduce the entropy