- Secured with a valid certificate from Let's encrypt
- No IP Leak
- No DNS Leak
- No request/send from/to external/third party sources
All you need: A CentOS 8 server with a domain.
Note 05/09/2021: If you had any problem, disable UDP and do not use the Anyconnect client app for a while!
Note 23/09/2021: Change the server or server IP every 3 months to prevent Google from tracking and flagging your server's IP.
Change the username-password list pass.txt (or create a new one) and then just run the command like this :
bash install.sh -f username-list-file -n host-name -e email-addressfor example :
bash install.sh -f pass.txt -n my.example.com -e mayemail@gmail.comNote: By changing the script, you can get a certificate without an email address. But it is better not to.
(--email $EMAIL_ADDR to --register-unsafely-without-email)
bash adduser.sh username-list-file
e.g. :
bash adduser.sh pass2.textcertbot renew --quiet && systemctl restart ocserv # && systemctl restart ocserv2Do you want to run ocserv on a new port with a different configuration? Take a look at copyoc.sh.
bash ./copyoc.sh -p <port>
e.g. :
bash ./copyoc.sh -p 8443Will block malware and adult content in the new VPN service
bash ./copyoc.sh -p <port> -f
e.g. :
bash ./copyoc.sh -p 2222 -f(reference: https://ooni.org/post/2019-iran-internet-blackout/#connecting-to-the-internet-from-iran)
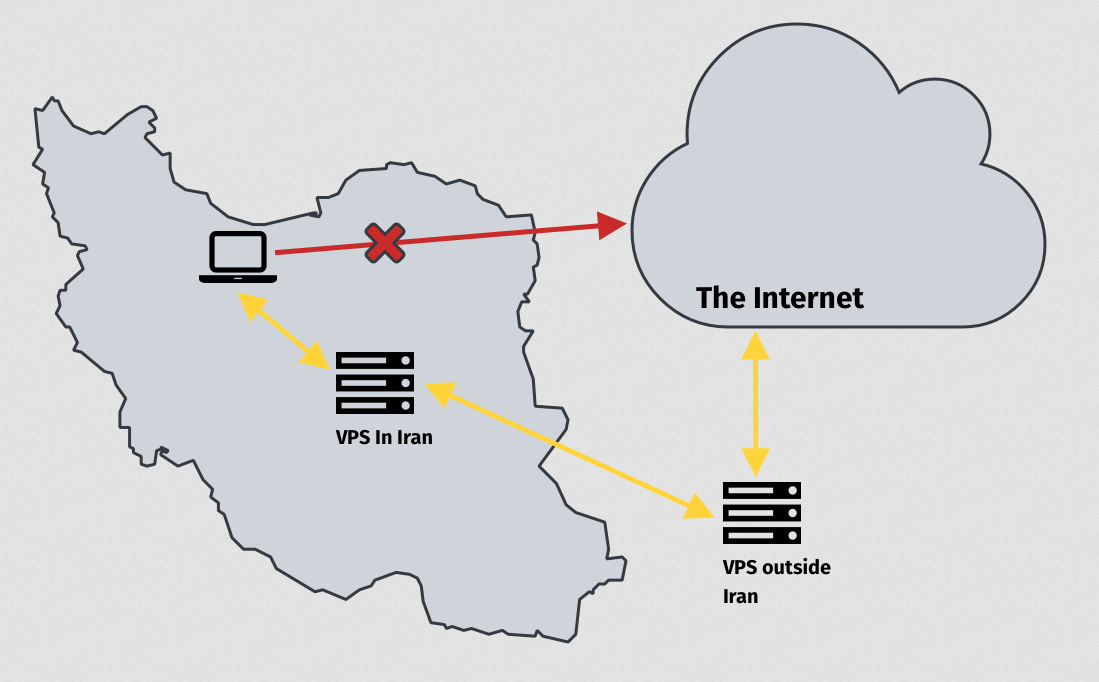
After installing Openconnect on a foreign VPS, just enter these commands on the domestic VPS:
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A PREROUTING -i eth0 -p tcp -m tcp --dport 443 -j DNAT --to-destination [foreignVPSip]:443
iptables -t nat -A PREROUTING -i eth0 -p udp -m udp --dport 443 -j DNAT --to-destination [foreignVPSip]:443
iptables -t nat -A PREROUTING -i eth0 -p udp -m udp --dport 53 -j DNAT --to-destination [foreignVPSip]:53
iptables -t nat -A POSTROUTING -o eth0 -j SNAT --to-source [domesticVPSip]
(Note: Make sure you use the correct network interface name. e.g. eth0 or enp0s3 or ... )
Then save iptables:
yum install iptables-services -y
systemctl enable iptables
service iptables save
systemctl start iptablesAnd then use Openconnect like this:
echo password|openconnect --resolve=domain.com:[domesticVPSip] -vu username --passwd-on-stdin https://domain.comOr temporary change A record to domestic VPS ip.
Note: The amount of incoming and outgoing traffic on your domestic VPS should not be equal.
Please let me know if there is any problem.